So, Marcel Lehel Lazar, aka Guccifer, the Romanian hacker is in FBI custody, he has been  speaking at length with agents investigating Hillary Clinton’s use of a private email account and private server which we now know contained 2,100 classified documents and he has told Fox News that hacking Hillary’s emails was…easy.
speaking at length with agents investigating Hillary Clinton’s use of a private email account and private server which we now know contained 2,100 classified documents and he has told Fox News that hacking Hillary’s emails was…easy.
For their part, the FBI is not commenting either on their conversations with the hacker or about any evidence they have regarding whether or not he actually managed to hack Hillary but there is evidence that he was in there.
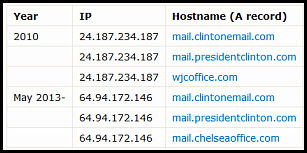
 Apparently, this Guccifer has revealed “doodles” drawn by Bill Clinton which were stored on the Clinton Foundation site and here’s why that is significant…Hillary’s clintonmail.com server, the private server in question, has the exact same IP address as presidentclinton.com and presidentclinton.com is the email of the Clinton Foundation.
Apparently, this Guccifer has revealed “doodles” drawn by Bill Clinton which were stored on the Clinton Foundation site and here’s why that is significant…Hillary’s clintonmail.com server, the private server in question, has the exact same IP address as presidentclinton.com and presidentclinton.com is the email of the Clinton Foundation.
And from Hillary herself…the server used at the Clinton Foundation is the exact same server she used during her reign of espionage as the Secretary of State.
Some reports are suggesting that there is no evidence that the server has or had been hacked but there could be a very good reason for that lack of evidence and that is where Hillary’s, now protected by immunity IT guy, Bryan Pagliano comes in. You see, Pagliano was an IT guy but NOT a cyber-security guy and from what I’ve been told…if Pagliano didn’t employ a slew of security measures to capture and track threats or hack attempts…the server could easily have been hacked without leaving so much as a trace of evidence.
The fact is, Pagliano didn’t put anywhere near adequate security on Hillary’s server as it lacked a intrusion prevention system, which means, there was no way for her system to track or identify hacking attempts and the way Guccifer got in was one of the most basic ways one could do it…
Guccifer accessed Sydney Blumenthal’s aol email account, followed IP addresses of emails sent to him and then sent emails TO those IP addresses that were bogus. If someone clicked into a link inside one of those bogus emails…Guccifer had everything he needed to access THAT email account and apparently…he did…because, as I reported months ago in an article, at one point, Hillary sent THIS email to someone in her office: “Neera–did you send me this? If not, I think your email address book has been hacked. If so, why?”
But it’s worse than you might think and while I don’t even pretend to have any deep understanding of how these things work, from what I’ve been told, and from what I’ve read, I don’t need to be an IT nerd to understand this and neither will you.
Without getting too deep in the technical weeds, let me try to explain this as simply as possible…
Hillary’s server, and her computer, had an open 3389 port which allowed remote use of her  system, called RDP or Remote Desktop Protocol, and that port is not secure in any way. It also connects, as I understand it, the server system’s various networks meaning that any computer, or email system networked through that server, as also easily accessed by the hackers. To put it another way, the open 3389 port was easily accessible and open to the entire internet.
system, called RDP or Remote Desktop Protocol, and that port is not secure in any way. It also connects, as I understand it, the server system’s various networks meaning that any computer, or email system networked through that server, as also easily accessed by the hackers. To put it another way, the open 3389 port was easily accessible and open to the entire internet.
To be clear…this has always been an issue and a very well publicized issue…this 3389 port business…and internet companies have, for years, advised companies not to leave that open lest they be vulnerable to hacking. Leaving it open, especially when one is dealing with 2,100 classified documents, is akin to being warned that keys to your front door have been distributed worldwide, the lock on your door doesn’t work properly and then you just leave it that way ignoring the distinct possibility that someday, you’ll come home and find that someone has broken into your home and stolen everything down to your last pair of socks.
So…what all was networked on that unsecured server?
All of that was 100% open to hackers and as I reported a week or so ago…Guccifer isn’t  the only one to have claimed to have had access to Hillary’s emails. There was also a Serbian hacker and the Russian intel community so it’s pretty clear that anybody who doesn’t necessarily like us, or who is allied with Russia, could have had access to anything and everything Hillary had in her private email system or stored on her private server.
the only one to have claimed to have had access to Hillary’s emails. There was also a Serbian hacker and the Russian intel community so it’s pretty clear that anybody who doesn’t necessarily like us, or who is allied with Russia, could have had access to anything and everything Hillary had in her private email system or stored on her private server.
As much as it galls me to say it, Hillary Clinton was our nation’s top diplomat for just better than 4 years and as the Secretary of State, Hillary was wheelin’ and dealin’ with allies and enemies alike…all the while using her private, unsecured server and email to conduct official, classified and in some cases, above top secret business.
Here’s the way to think about this…
Let’s say you’re playing chess…hundreds of chess games all at the same time…and the idea is to win every game because, if you don’t, really bad things are going to happen. Part of this chess tournament, is that whatever one of your opponents does, whatever move they make, has an effect on every move many of your other opponents make as well as the moves you make.
Before every move you make, you have assistants whispering in your ear, telling you what move to make next based on the moves your other opponents are making or the moves your assistant’s believe they’re about to make, thus making your next move even more important, but the advice you’re getting whispered into your ear, how you’re going to move, is being forwarded to each and every one of your opponents ahead of your move.
How many games of chess, in this high-stakes tournament scenario, can you expect to win?
Hillary shook hands with North Korea and they promised her that they wouldn’t conduct any more nuclear tests. How did that work out? Hillary pressed the reset button with Russia. How did that work out?
 Hillary corresponded with others regarding our security in Benghazi, about drawing down our personnel in Benghazi, about hiring our enemies in a time of war to replace our own security in Benghazi and about the whereabouts of Ambassador Stevens in Libya and specifically in Benghazi.
Hillary corresponded with others regarding our security in Benghazi, about drawing down our personnel in Benghazi, about hiring our enemies in a time of war to replace our own security in Benghazi and about the whereabouts of Ambassador Stevens in Libya and specifically in Benghazi.
How did all of that work out?
All of this leaves us with some important questions…
Was Hillary’s system, her email and her server, hacked? Obviously, yes, and not just by Guccifer but by just about anybody who wanted to read her documents including friends and foes alike.
Did Hillary’s private server have adequate security protecting it and her documents? Obviously, no it did not.
Did Hillary have classified documents on that private server? Yes…at least 2,100 of them and some of those were SAP or above top secret which means that Guccifer and our friends and foes alike all had access to them.
Is storing or sending and receiving government documents, classified or otherwise, on an unsecured private server a crime? Yes…it is in violation of the Federal Records Act.
Did Hillary intentionally allow access to government documents, including classified and SAP documents and is that a crime? As Hillary intentionally set up a private server and intentionally set up her own private email account on that server, and as Hillary failed to follow any security protocols whatsoever in doing so, a strong case should be able to be made that she did, intentionally set into motion the process by which her system could be hacked…at best, she is guilty of gross negligence in this, and gross negligence is also against the law with regard to official government document storage.
You can read the statute regarding such gross negligence here.
Did Hillary commit espionage?
This is somewhat more complex than a simple yes or no answer and to grasp what we’re talking about here, we need to ask other questions…like…did Hillary steal official  government documents including classified, top secret or SAP above top secret documents?
government documents including classified, top secret or SAP above top secret documents?
Somehow, those documents, those SAP documents did make their way onto Hillary’s private, unsecured system and, as I have positioned before, it seems she had an accomplice within the NSA who was able to grab those documents and send them TO Hillary BEFORE they were marked SAP or classified in any way so…it seems pretty obvious that Hillary KNEW they were classified, knew to what extent they were classified and knew that outside a secured system in a secured location neither she, nor anyone else should have had access TO those documents. And yet…there they were…on Hillary’s private, unsecured system, for the whole world to see.
Once on Hillary’s unsecured system, who had access to the classified and SAP documents other than hackers and other country’s intel communities? Apparently…all of her advisors, like Huma Abedin, her deputies, like Cheryl Mills and Patrick Kennedy, her IT guy, Bryan Pagliano and of course, Sydney Blumenthal and her attorney, David Kendall and we know for a fact that many of those within the Clinton inner circle completely lacked the security clearance to have ever laid eyes on those documents. In fact, people like Abedin, Mills, Kennedy and Blumenthal were also sending and receiving such classified documents to and from Hillary herself.
And there is recent precedent regarding espionage…
The federal government has charged Ed Snowden with espionage…the “unauthorized communication of national defense information” and “willful communication of classified communications intelligence information to an unauthorized person,” which, considering to whom and from whom Hillary was sending and receiving documents, falls in line with Snowden’s activities…not to mention that Snowden was showing the documents he stole to our friends and foes and Hillary’s unsecured system was open to friends and foes.
communication of national defense information” and “willful communication of classified communications intelligence information to an unauthorized person,” which, considering to whom and from whom Hillary was sending and receiving documents, falls in line with Snowden’s activities…not to mention that Snowden was showing the documents he stole to our friends and foes and Hillary’s unsecured system was open to friends and foes.
So…as per law, government documents, classified or otherwise, are to be stored on secured systems under the control of the government, and as Hillary intentionally saw to it that any and all documents generated by herself or that were passed to her by others were NOT so stored…yes…Hillary did steal government, classified, top secret and above top secret documents.
But, did she INTENTIONALLY make them available to the intel communities of other countries?
Let’s review…Hillary intentionally set up her own private server and her own private email  account…intentionally used it exclusively, never once using a secured .gov account…was at the very least, grossly negligent in not having her unlawful private server or email account come anywhere close to meeting official security protocols…intentionally shared official, classified, top secret and SAP documents with others, some of whom held no clearance to have laid eyes on said documents and intentionally allowed others, connected by networking their systems to her unlawful private, unsecured system, to share documents and communications with one another.
account…intentionally used it exclusively, never once using a secured .gov account…was at the very least, grossly negligent in not having her unlawful private server or email account come anywhere close to meeting official security protocols…intentionally shared official, classified, top secret and SAP documents with others, some of whom held no clearance to have laid eyes on said documents and intentionally allowed others, connected by networking their systems to her unlawful private, unsecured system, to share documents and communications with one another.
Now, add to all of that, two other very important facts in establishing intent…
- At no time, during her years as the Secretary of State, did Hillary Clinton allow any Inspectors General to operate inside the State Department and this is a key piece of evidence, as an Inspector General would have been the one to identify the issue, i.e. Hillary’s use of a private, unsecured server and email account…would have been the one to blow the whistle and the one to have put a stop to her private system use, in accordance to the law, from the word go. Hillary’s disallowing of Inspectors General in the State Department for the complete time she operated as Secretary of State…was indeed intentional….and certainly appears to have been done so that she, Hillary Clinton, could operate above the law.
- While emails to and from Hillary’s IT specialist, Bryan Pagliano, who was also, during her entire reign at the State Department, the State Department’s IT specialist, do exist from the period of time AFTER Hillary’s reign ENDED…there is not a single email to or from Pagliano DURING Hillary’s time at State in existence. He was the IT specialist for the ENTIRE State Department, as well as HILLARY’S PERSONAL: IT specialist…and there’s not one single email to him or from him to be found…which means ALL emails to or from Pagliano have been scrubbed from that private, unlawful server in Hillary’s purge of some 30,000 “private” messages.
Obviously, there were things in emails between herself and her minions and Pagliano she didn’t want anyone to see.
So, did Hillary Clinton commit espionage?
Because of her intentional efforts to store classified and above top secret documen ts away from government controlled secure systems, because she didn’t provide even the most basic security on her unlawful private system, because she shared those documents with others who didn’t have the proper security or any security clearance and because she intentionally disallowed government oversight, an Inspector General to be inside the State Department throughout her entire reign there…and as a result, her system was hacked, and those documents, including the SAP documents were then open and available to our friends and enemies alike…and because she obviously attempted to cover her tracks with regard to purging 30,000 emails, including every single email to or from her IT specialist, Bryan Pagliano…yes, Hillary committed espionage against the United States.
ts away from government controlled secure systems, because she didn’t provide even the most basic security on her unlawful private system, because she shared those documents with others who didn’t have the proper security or any security clearance and because she intentionally disallowed government oversight, an Inspector General to be inside the State Department throughout her entire reign there…and as a result, her system was hacked, and those documents, including the SAP documents were then open and available to our friends and enemies alike…and because she obviously attempted to cover her tracks with regard to purging 30,000 emails, including every single email to or from her IT specialist, Bryan Pagliano…yes, Hillary committed espionage against the United States.
Various intel agencies are now in the process of doing damage assessments, something they do only AFTER national security intel has been breached and/or compromised. Bryan Pagliano has immunity and has been singing like a canary. Guccifer, the hacker, is in FBI custody and has been talking for over a week now and over the next few weeks, the FBI will be interviewing Hillary’s closest aides and will indeed, be interviewing Hillary herself. This is what they do near the end of an investigation and they will only be asking questions to which they alre ady know the answers to determine whether or not the witnesses are being truthful.
ady know the answers to determine whether or not the witnesses are being truthful.
The Hill reports that Bradley Moss, a National Security Attorney said, “The extent to which the person intended to remove classified documents is irrelevant. All that matters for strict legal purposes of culpability is whether the person, by virtue of their official position, came into possession of classified information and affirmatively removed the information to an unauthorized location (i.e., the private server). Whether the person knew or suspected the information was classified is irrelevant.”
Let me put this another way…if the DOJ fails to charge Hillary after this investigation is completed, then they have absolutely no business in ever charging Snowden or any other American citizen, should any of us do what Hillary did, and that would make it open season on our national security. Further, it would mean that we are living under tyranny , where government officials are free to do what would land ordinary citizens in a federal prison.
, where government officials are free to do what would land ordinary citizens in a federal prison.
The outcome of this FBI investigation, and how the DOJ responds will provide the answer to one final question…
Is it time to water the tree of liberty?
SPECIAL NOTE!!
As my partner and friend, Diane Sori, is still in FB jail for the next 14 days, I urge you to click on the link and read her latest op-ed “The Blame Game Begins” and please share both her article and mine. Thanks so much!!!